Preventative Computer Maintenance

The best way to avoid major problems is to stop them from happening in the first place. That’s where preventative maintenance comes in.
A good preventative maintenance program incorporates a comprehensive backup plan, measures to secure the system against malicious viruses, as well as periodic hardware and software maintenance. The goal is to reduce the likelihood of hardware failures, extend the useful life of your system, minimize system crashes caused by outdated drivers and other software problems, secure the system against viruses and other malware, and most importantly, prevent crucial data loss.
The following steps outline a basic preventative maintenance program that you can use to keep your system running at optimal settings and avoid any regrets from unexpected and often unrecoverable crashes.
Backing up the system
Maintaining a good set of backups is a critical part of preventative maintenance.
The availability of inexpensive hard drives and motherboards that support RAID 1 mirroring had led many people to depend solely on RAID 1 to protect their data. That’s a very bad idea. RAID 1 protects only against the failure of a hard drive, which is partial protection at best. RAID 1 does nothing to protect against:
- Data being corrupted by viruses or hardware problems
- Accidentally deleting, overwriting, or modifying important files
- Catastrophic data loss, such as fire or theft of your equipment
To protect against those and other threats, the only reliable solution is to make backup copies of your data periodically to some form of removable media, such as CDs, flash drives, external hard drives, and now iCloud, a very popular and commonly used storage solution these days, that “follows” you wherever you go, and without the risk of losing your storage hardware to theft or misplacement between travels commutes.
You Can Never Be Too Well Backed Up
Whatever backup means and methods you use, keep the following in mind and you won’t go far wrong:
- Back up frequently, particularly data that is important or hard to reconstruct
- Verify backups to ensure that they are readable and that you can recover the data from them
- Maintain multiple backup sets, and organize by date for redundancy and to permit recovering older versions of files
Although online backup services like GoogleÂ’s Gmail are reasonable choices for supplemental backups, we suggest that you not use them as your primary form of backup. There are too many things that can go wrong, from your (or their) Internet connection being down to server problems at the hosting company. When you need your backups, you need them right now. Keep your primary backups within easy reach.
Software Security Isn’t
Although many people depend on software firewalls, such as ZoneAlarm (http://www.zonealarm.com) or Norton Internet Security (http://www.symantec.com), we think that’s a mistake. Among security experts, it’s a truism that software cannot protect the system that is running it. Any software firewall may be compromised by exploits that target it directly or the underlying operating system. In our opinion, a software firewall is better than nothing, but not much better.
Securing the system
The most important step that you can take to secure your system against worms and other malicious intruders is to install a hardware router/firewall between your system and the Internet. A properly configured router/firewall blocks malicious scans and probes, and makes your system effectively invisible to the millions of infected systems on the public Internet that are constantly trying to infect it. Hardware router/firewall devices typically sell for only $30 to $50, so they are cheap insurance against your system being compromised by malicious intruders.
We much prefer cable/DSL routers made by D-Link, such as the DI-604 (wired only) or the DI-624 (wired/wireless), but similar broadband routers made by NETGEAR and Linksys are also popular. All current models we are familiar with use default settings that provide adequate security, but it’s still worth taking a few minutes to study the manual to make sure that your router is configured to provide a level of security that is acceptable to you.
WEP Security Isn’t
If you install a wireless router and enable wireless networking, be sure to secure it properly. The standard used by early 802.11 wireless devices, called WEP (Wired Equivalent Privacy) is now hopelessly insecure. WEP can be cracked in literally minutes or even seconds using utilities that anyone can download. The newer WPA (Wi-Fi Protected Access) standard, when configured properly, is secure against all but the most sophisticated attacks. If your current wireless adapters and access points support only WEP, replace all of them immediately with devices that support WPA. Otherwise, you might as well run your wireless network with no security at all.
Here are some other steps you should take to secure your Windows systems:
Install Firefox.
One of the most important steps you can take is to secure a Windows system is to replace the buggy, insecure Internet Explorer with a different default browser. The most popular alternative browser is Firefox (http://www.mozilla.org). We suggest that you install Firefox immediately and begin using it as your default browser. Ignore the Microsoft-inspired FUD that argues that Internet Explorer is just as secure as Firefox. It isn’t. Firefox is an order of magnitude more secure.
Install ad-blocking software.
Although most banner ads and pop-ups are not malicious, they are annoying. And some ads contain links to malicious sites where merely clicking on a link or even simply viewing the page may install malware on your system via a “drive-by download.” Using ad-blocking software minimizes the problem.
New viruses are constantly written and released, so it’s important to run a virus scanner regularly and keep it updated with the latest virus signatures. Although Norton AntiVirus (http://www.symantec.com) and McAfee VirusScan (http://www.mcafee.com) are two of the most popular antivirus scanners; we don’t use either. Instead, we recommend installing Grisoft AVG Anti-Virus (http://www.grisoft.com). AVG is as effective as any competing product we’ve used, places few demands on system resources, and is free for personal use.
Hard drive housekeeping
As we started to write this section, we checked one of our hard drives. It had 175,503 files in 11,687 folders. It’s anyone’s guess as to what they all are. Some are programs and system files, of course. We know there are hundreds of documents and spreadsheets, and thousands of audio files, images, and so on. But the majority of those 185,503 files are probably temporary and backup files, duplicates and older versions of current datafiles, browser cache files, and similar garbage. All they do is clutter up the hard drive, wasting space and harming disk performance. They need to be pruned from time to time, if only to keep them from eating you out of house and home.
Disk Fragmentation
The solution to disk fragmentation is to run a defragging utility periodically. A defragging utility reads each file and rewrites it contiguously, making file access much faster. The Disk Defragmenter utility bundled with Windows is slow, inefficient, and feature-poor. But, hey, it’s free, and it’s (usually) good enough to do the job.
Keeping your system updated
Hardware and software companies periodically release updated software, device drivers, and firmware. These updates may be security related, or they may add support for new features or compatibility with new devices. We recommend that you keep yourself informed about such updates, but the Golden Rule when it comes to installing updates is, “If it ain’t broke, don’t fix it.”
These are just a few measures to take, among many others, and since most users are not experts, the best way is to take your computer to the nearest computer repair (Smartfix Link) shop at the earliest sign of security threat or slowing down.
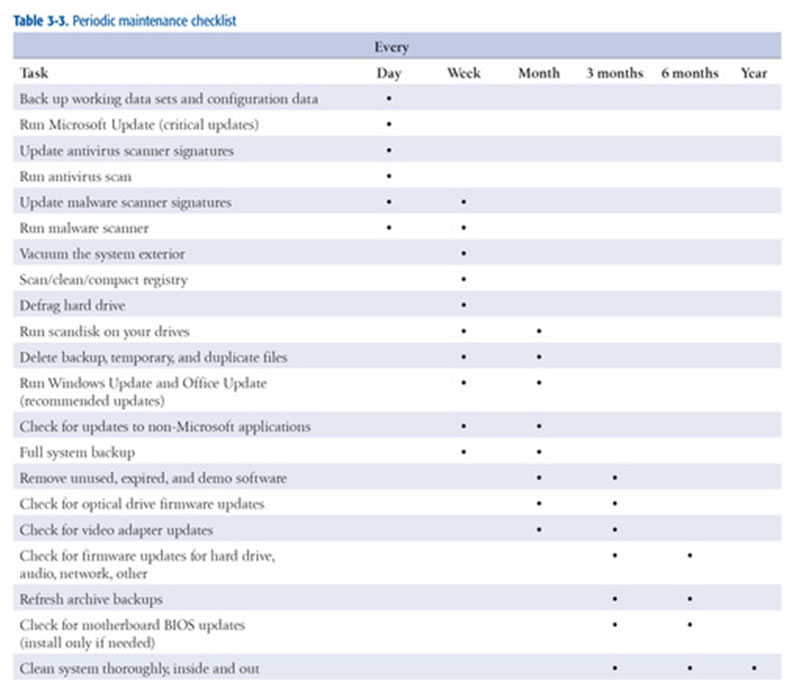
Here is a periodic maintenance checklist to help you keep your system threats at bay for as long as possible:
The following table summarizes the procedures we recommend for periodic maintenance.